 iPage is considered as the best web hosting provider because it's established from very soon in the industry of web hosting, since 1998. So they provide the affordable web hosting package for all purposes of bloggers, websites, online portals, etc.
iPage is considered as the best web hosting provider because it's established from very soon in the industry of web hosting, since 1998. So they provide the affordable web hosting package for all purposes of bloggers, websites, online portals, etc.
iPage only offers one web hosting plan to all customers, with features: free domain name for first year, UNLIMITED hosted domains/websites, no limit of disk storage/bandwidth, iPage easy site builder,free advertising credits (up to 175$), etc.
Most important, when you register the web hosting at iPage through our link, we're going to issue a full refund to you. That's awesome! You may try iPage web hosting for FREE now!
 If your browsers disabled JavaScript for some reason but you do not know how to turn JavaScript on, javascriptON may help you enable JavaScript in many browsers of many platforms: PC, mobile, tablet.
If your browsers disabled JavaScript for some reason but you do not know how to turn JavaScript on, javascriptON may help you enable JavaScript in many browsers of many platforms: PC, mobile, tablet.
javascriptON.com detects your browsers exactly to provide best proper advices. Just type javascriptON.com into address bar then follow their instructions to activate JavaScript. Or you may choose a specified browser to see the instruction:
- Enable JavaScript in Internet Explorer
- Activate JavaScript in Firefox
- Instructions to enable JavaScript in Google Chrome
- Quick actions to enable JavaScript in Opera
- Learn to enable JavaScript in Safari
 Whether we are talking about an online company or a land based one, logo design is an important matter.
Whether we are talking about an online company or a land based one, logo design is an important matter.
The logo will appear on all the documents of the company, on the site, on the greeting cards, on different flyers and other promotional materials you might distribute.
This is why it is important to choose the colors and the right forms with the activity of every client, and with the message that must be transmitted with this logo.
 What sets TechJobs.com apart is collaboration with local tech recruiters and targeting only the best of the best tech talent in the hottest niches such as: video game development, Internet application development, Java development, database administration, cloud computing, smart grid technology and more. Recently tech jobs added featured job listings for top tech companies to obtain great exposure to attract top tech talent searching for new positions. Additionally a tech resources area was added that includes tech tutorials and tech news.
What sets TechJobs.com apart is collaboration with local tech recruiters and targeting only the best of the best tech talent in the hottest niches such as: video game development, Internet application development, Java development, database administration, cloud computing, smart grid technology and more. Recently tech jobs added featured job listings for top tech companies to obtain great exposure to attract top tech talent searching for new positions. Additionally a tech resources area was added that includes tech tutorials and tech news.
 Finally the long awaited Samsung Galaxy Nexus is available for sale in the US market under contract with Verizon Wireless. The price of Galaxy Nexus at present is $299 with a two year contract with Verizon Wireless while Skyrocket is available for $149.99 along with a two year contract with AT&T.
Finally the long awaited Samsung Galaxy Nexus is available for sale in the US market under contract with Verizon Wireless. The price of Galaxy Nexus at present is $299 with a two year contract with Verizon Wireless while Skyrocket is available for $149.99 along with a two year contract with AT&T.
Due to the combination of these two operating systems, Ice Cream Sandwich would run perfectly well on both smartphones and tablets. Among the top devices form Samsung, Samsung Galaxy S2 Skyrocket is also a remarkable device which happens to be the LTE version of Galaxy S2. The OS for Skyrocket happens to be Gingerbread which at present is running on most of the Android based phones.
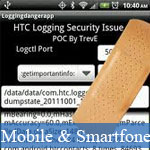 HTC smartphones running Android are considered to be among the very best mobile devices available in the market. HTC's collaboration with Android has reaped considerable benefits for both these companies and HTC has been releasing some of the finest high end devices. But just when everyone was talking about the location tracking flaw that was recently pointed out in iOS, it seems that recent Android based HTC devices have a serious security flaw that is most probably even serious than the one found in iOS. This latest issue was discovered by developers at Android Police in collaboration with Trevor Eckhart and it seems that most of the recent giant tech devices released by HTC including EVO 3D, Radar, Sensation and Vivid are infected with this problem.
HTC smartphones running Android are considered to be among the very best mobile devices available in the market. HTC's collaboration with Android has reaped considerable benefits for both these companies and HTC has been releasing some of the finest high end devices. But just when everyone was talking about the location tracking flaw that was recently pointed out in iOS, it seems that recent Android based HTC devices have a serious security flaw that is most probably even serious than the one found in iOS. This latest issue was discovered by developers at Android Police in collaboration with Trevor Eckhart and it seems that most of the recent giant tech devices released by HTC including EVO 3D, Radar, Sensation and Vivid are infected with this problem.
At present, all the major HTC phones log under user data including email addresses, SMS data, location, phone numbers, system logs, etc. through a variety of logging tools that have been made available by default in all these devices.
 A renowned Apple hacker, Charlie Miller, has warned that there is a serious bug present in iOS which can cause a lot of damage to the users downloading applications from Apple's app store.
A renowned Apple hacker, Charlie Miller, has warned that there is a serious bug present in iOS which can cause a lot of damage to the users downloading applications from Apple's app store.
According to Charlie, this bug can let the hackers to have control over the iOS devices of the users which can eventually lead to further damage such as having an access to their contacts, photographs and other important documents present in the device. What's more, users won't even know that the security of their device has been breached and their important information has been accessed.
 There are perks to being a programmer (especially if you're one of few in the office). Aside from being seen as a mysterious internet-whisperer who can magically make computers behave, you have the power to liven up the dreary cubicle farm. All you need are a few JavaScript snippets of code, a coworker's vacant office cubicle, and a ninja suit. Okay, scratch the suit...that might be too obvious.
There are perks to being a programmer (especially if you're one of few in the office). Aside from being seen as a mysterious internet-whisperer who can magically make computers behave, you have the power to liven up the dreary cubicle farm. All you need are a few JavaScript snippets of code, a coworker's vacant office cubicle, and a ninja suit. Okay, scratch the suit...that might be too obvious.
If you've never used a browser hack or even JavaScript, these JavaScript hacks are still easy enough to use: just copy and paste over the current page's URL. Basically, these JavaScript snippets work perfectly on Firefox 3+ but note that this does not work in all browsers and platforms equally, so do a little testing before you attempt your diabolical schemes.
Here's 3 funny JavaScript pranks you'll be happy to make with your coworkers: Make Web Browser Editable, Complete Browser Freak Out and Buzzing Swarm of Images. These JavaScript pranks and more funny JavaScript effects can be found easily at 9 Funniest JavaScript effects if you still need.
 Whether you're new to jQuery or are simply reevaluating the way you use it, it's worth looking into the most practical way to load it onto your website. Up until a few years ago, the only option was to upload a copy into each website's directory.
Whether you're new to jQuery or are simply reevaluating the way you use it, it's worth looking into the most practical way to load it onto your website. Up until a few years ago, the only option was to upload a copy into each website's directory.
Now, a myriad of web-hosted options are available, the most popular of which is Google Libraries API, a content distribution network for common JavaScript libraries, including jQuery. Of these two options, which is the best solution for your development needs? The best way to answer this question is to take a look at some of their features side-by-side.
Please go to the inner post-page for full questions & answers to choose the best jQuery solution. Or read more other posts:
- Awesome and Advance JavaScript Tutorials
- Reuse JavaScript codes as jQuery Plugins: Tutorials and Examples
- 5 Good JavaScript Habits for Better Improvement
 If you are a person who takes your most time in front of your computer, or you are a business person who runs your business with online way, then it is time for you to consider about Fireeye.com as your address in order to protect your data and important files from any cyber attacks that many can be found at Internet today.
If you are a person who takes your most time in front of your computer, or you are a business person who runs your business with online way, then it is time for you to consider about Fireeye.com as your address in order to protect your data and important files from any cyber attacks that many can be found at Internet today.
You know, since Internet has been being an open way for everybody to transfer their data to everywhere, it is actually easy for an irresponsible person to attack our data through any holes that may exist on our traditional old security system. Well, you should know that the technology of networking has been increased so well today. It is natural if the threats do also have been improved since knowledge about computer system has also increased as well.
 As the holiday season quickly approaches, thoughts turn to hot chocolate, stories of Santa Claus, and hurried gift purchasing. Christmas songs start dominating radio stations, and children everywhere finish off the final preparations for their holiday programs. Check our older posts for Christmas:
As the holiday season quickly approaches, thoughts turn to hot chocolate, stories of Santa Claus, and hurried gift purchasing. Christmas songs start dominating radio stations, and children everywhere finish off the final preparations for their holiday programs. Check our older posts for Christmas:
- 25 Awesome Christmas Worpress Themes for 2010
- Christmas iPhone Applications: Bests for Virtual Reality
- Christmas Social Media icons: Bests of
- Top 10 Beautiful Christmas Countdown Timers
- More 10 Awesome Countdown Timers to Christmas 2010
The world of Android apps is certainly not exempt from spreading Christmas cheer. In fact, a number of fun apps are available for your Android phone; check out the following Christmas Android apps for ways to keep even your technology-loving self full of the Christmas spirit.
Today, our writer - Blake Sanders is happy to share with you some best-reviewed Andriod apps for this Christmas 2011, he wrote this post for 9BlogTips.com, please go to Christmas 2011 Ready with Awesome Android Apps for FREE to read more details.
 As more wireless providers and Internet providers begin to offer the iPhone, the device's growing reach means that it is the subject of an increasing number of security risks and threats to personal information and data. The number of mobile apps for the iPhone means that more and more people are able to use it, develop for it, and exploit its growing popularity.
As more wireless providers and Internet providers begin to offer the iPhone, the device's growing reach means that it is the subject of an increasing number of security risks and threats to personal information and data. The number of mobile apps for the iPhone means that more and more people are able to use it, develop for it, and exploit its growing popularity.
In a culture of malicious opportunists, it's important to stock your iPhone with a few key applications that will prevent your personal information from becoming public, and prevent your device from being used as part of a larger scheme to defraud iPhone users around the globe. Luckily, Apple's App Store is full of applications which will keep your iPhone - and its integrity - intact. In this post, jsB@nk would like to present you a list of 5 best security iPhone apps: Accellion, iDiscrete, Symantec ThreatCon, Mobile Active Defense and Threatpost.
Save up to 630$ when buy new iPhone 15
GateIO.gomymobi.com
Free Airdrops to Claim, Share Up to $150,000 per Project
https://tooly.win
Open tool hub for free to use by any one for every one with hundreds of tools
chatGPTaz.com, chatGPT4.win, chatGPT2.fun, re-chatGPT.com
Talk to ChatGPT by your mother language
Dall-E-OpenAI.com
Generate creative images automatically with AI
AIVideo-App.com
Render creative video automatically with AI






 06/04/2013
06/04/2013 0
0
